World’s worst ransomware attack yet
Aractus
The recent WannaCry ransomware attack has been described as being the worst attack yet. The cybercriminals who created it have quickly become the world’s most wanted cyber criminals… but let’s talk about who’s responsible here, because the cyber criminals were armed whether intentionally or not by the NSA.

By the way, I have been working on a little project that is nearing completion, here’s a little preview of it that I made very quickly using Microsoft GIF Animator:

I highly recommend installing uBlock Origin, that will provide you with some protection again an infection through malvertising.
The NSA developed an arsenal of cyber weapons. One of these weaponisd exploits is called EternalBlue. The NSA’s entire arsenal of cyber weapons was both leaked and sold to third parties, including to hacking groups. Recently, a different arsenal of cyberweapons developed separately by the CIA was leaked to Wikileaks (known as Vault 7) who proceeded with responsible disclosure. Responsible disclosure means giving broad information to the public, while giving specific information to affected software and hardware vendors so that vulnerabilities can be patched, and then later full disclosure. In the case of the NSA’s arsenal of cyber weapons, it fell into the hands of a hacking group called The Shadow Brokers, and they do not believe in responsible disclosure so they promptly dumped the cyber weapons directly into the hands of the masses. The Shadow Brokers claim they hacked the NSA and stole the weapons, but however they came to obtain them is irrelevant.
The reason this is the worst ever malware attack is that it has crippled critical infrastructure. This is what every security expert has been worried about. It leverages EternalBlue (and EsteemAudit for older OS’s) to spread across computing networks. How ordinary users becomes infected though has not yet come to light, but I suspect Malvertising may be one culprit.
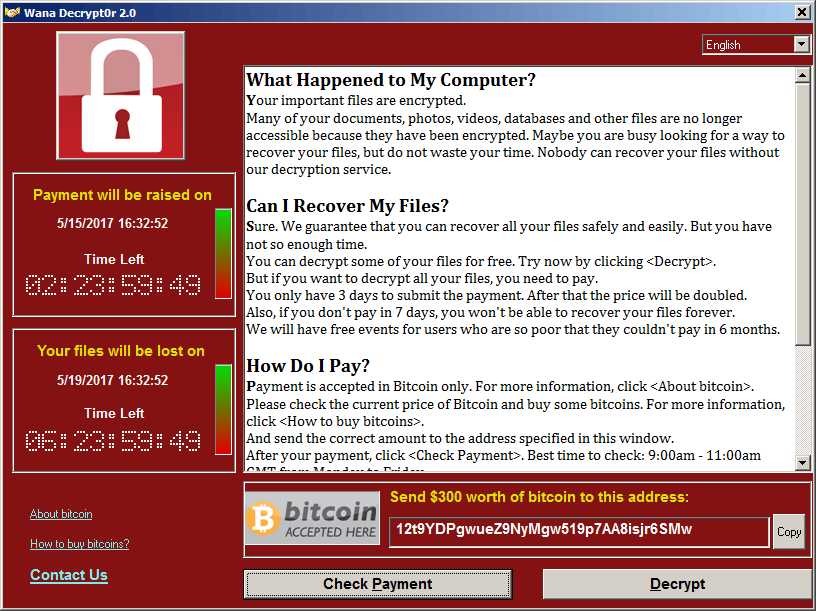
Ransomware works by encrypting your data using RSA encryption. What you need to know about RSA is that it’s the same principle behind SSL/TLS internet security. It is an asymmetric encryption – there are two keys, let’s call them Key A and Key B. If data is encrypted with Key A, then it can only be decrypted with Key B. If it’s encrypted with Key B, it can only be decrypted with Key A. Ransomware generally generates a unique key pair for each and every infection, and it can be remotely generated on a server far away. What that means is that an infected user has no way of obtaining their decryption key – it can’t be brute-forced, it can’t be extracted from the program, the only way to get it is from the cybercriminals who have it.
If you’re infected- should you pay up? Well, if your data is worth more to you than $400 – yes you should. Some reports have suggested you have no guarantee or receiving a decryption key… well that’s true, but generally speaking operators of ransomware do provide the decryption keys when payments are made. The situation where that might not be true is if you manage to get infected with an older malware by a group that’s no longer active, then I would agree you would be chancing it if you pay up.
So who should foot the bill for this? I believe the US government should be held to account, and made to pay out the ransoms. They’re the assholes that developed this cyberweapon. This is exactly the reason why the security industry hates the so-called intelligence industry. The correct thing to do when you find a security vulnerability is to do exactly what Wikileaks did with Vault 7: engage in responsible disclosure so that the vulnerabilities can be patched. Think about it this way, the NSA is a foreign intelligence agency that we would classify the same way as any other cyber criminal organisation. If they develop a weapon, then you can bet that someone else – whether in China, in Russia, in India, or elsewhere has also developed it. And even if they haven’t, as we’ve seen time and time again these inevitably get leaked/stolen.
And WannaCry has crippled critical infrastructure – that’s one of the worst possible outcomes of a cyber attack. Hospitals, schools, and telecommunications were taken out with this purely as a side-effect of its original intention. Had the cyber criminals wanted to though they could have specifically launched a far more vicious attack specifically aimed to take out critical infrastructure, and if that was done there could have been thousands of deaths as a consequence: rioting could have happened in cities across the world if power grids were taken off-line for example.
You may have heard that a security researcher that calls himself MalwareTech “accidentally” stopped WannaCry from spreading further. Well, that’s a half-truth. He did a write up on his blog about it actually. In a nutshell, the malware checks for the existence of a “random” domain that doesn’t exit. If an IP address is returned then it assumes it’s being run in a sandbox and shuts down its operations – this is a tactic it uses to try and evade malware detection by anti-malware software executing the program in a sandbox. It effectively is a kill-switch, but not intentionally so. But to say that it was accidental is not true, as stated clearly on the blog it’s standard practise to register domains found within malware as it gives researchers a way to track malware as much as anything else.