What you weren’t told about WannaCry
Aractus
I pride myself on providing you, the humble visitor, with good information. Not always perfect because, well, I’m not a security expert. You can think of this post as an afterthought if you like to my previous post, what I am aiming to do here is complete the picture.
Is Microsoft to blame?
The US Government and their spy agency the NSA are the main guilty parties in this instance. The ShadowBrokers who hacked the NSA and then publicly released the weaponised exploit are also to blame. And yes, Microsoft absolutely shares some of the culpability. Here is the thing you haven’t been told anywhere on the internet… some systems don’t update even when configured to do so. You want evidence? Here are screenshots I took earlier this week on a friend’s PC:
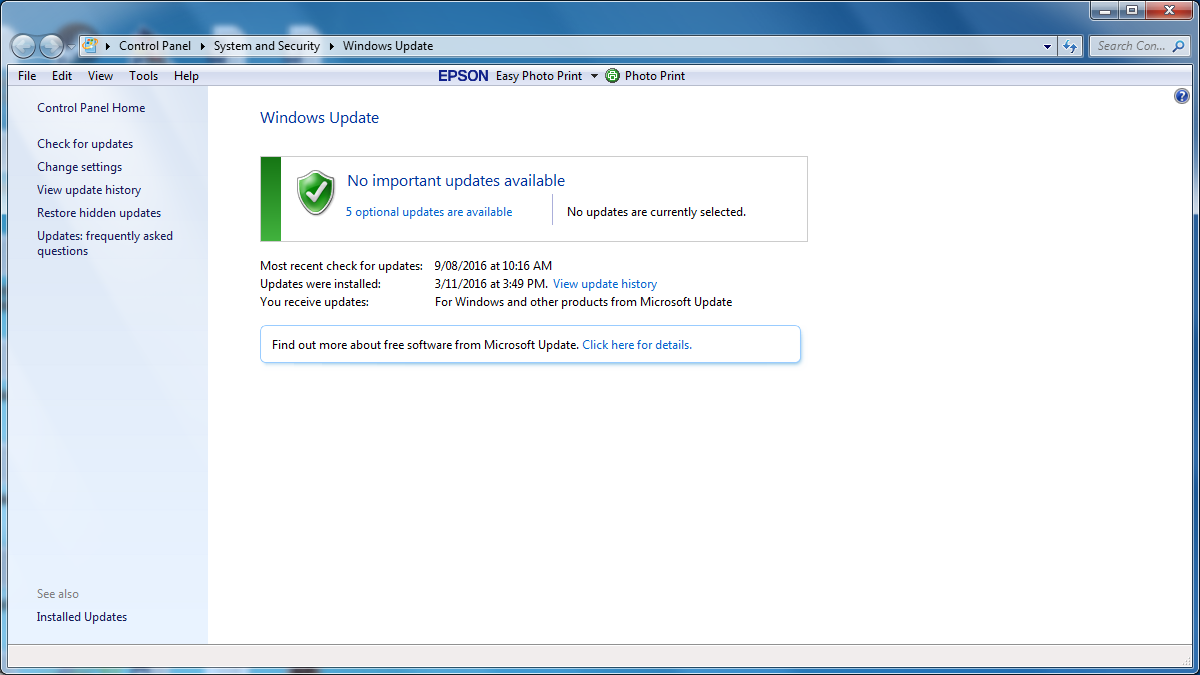
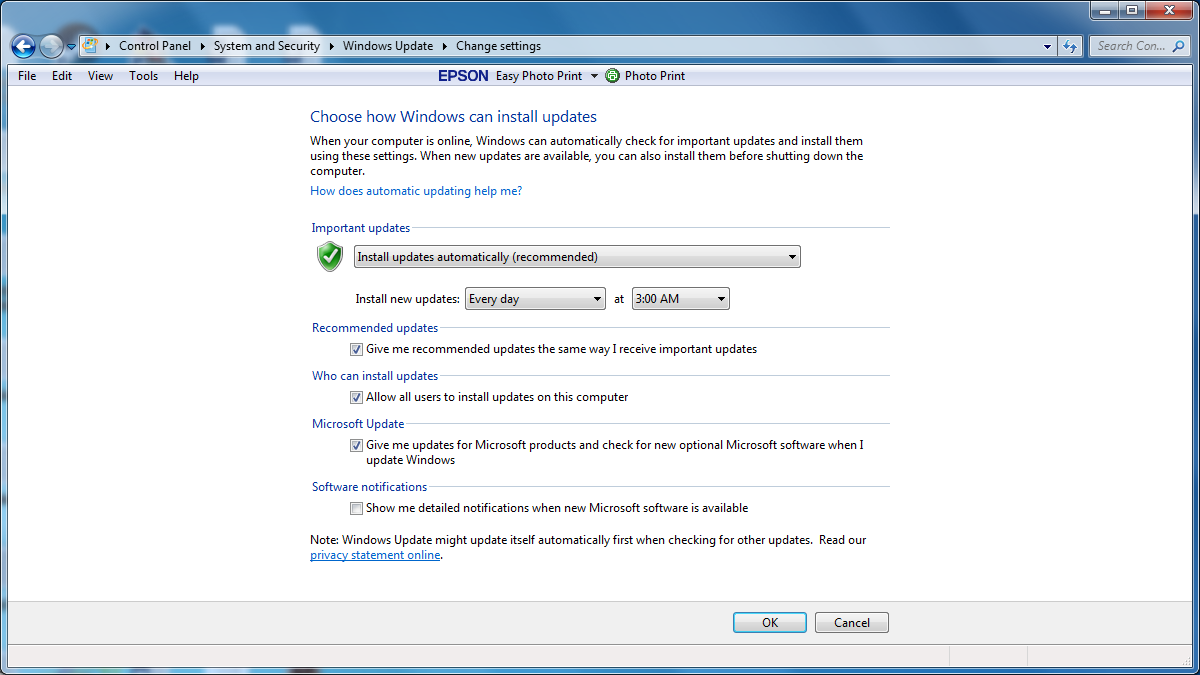
When I manually checked for updates it just spent hours on this screen:
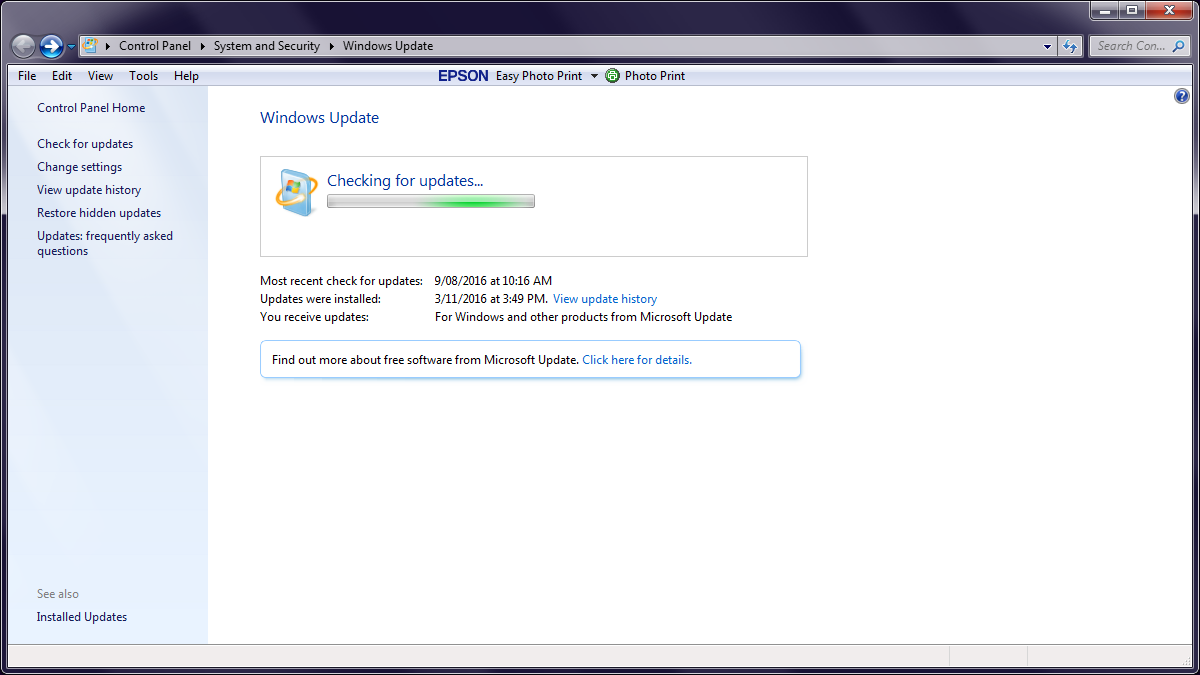
And no, that system is not patched. I was unable to fix the problem. WHAT THE FUCK MICROSOFT?! My solution for that system will be to re-install Windows. Nothing worked – and I did try. This page contains most of the fixes I tried. The owner of that PC had no idea the system wasn’t up to date. How many other Windows installations have this same problem?
And probably the most misreported fact on the internet “windows doesn’t support XP anymore”… WRONG! They do. They only provide support to those who pay for it though, and according to some the latest pricing for this privilege is about USD 1000 per year per desktop Windows XP installation. For the ordinary home user, you can still get Windows XP updates until 2019, and possibly longer. To achieve this you simply tweak a registry setting that tells Microsoft that it’s an Embedded system. XP was embedded into all kinds of hardware that is impossible to upgrade – speciality hospital equipment like MRI scanners, ATMs, etc. And they still receive security updates to this day.
People were surprised when Windows released a patch for this vulnerability for Windows XP. But they shouldn’t be – the patch would have been rolled out for XP Embedded at the same time as Windows 7/8/8.1. The only difference is that they waited until after the worm appeared before pushing the patch to non-embedded XP systems.
Why was there a kill switch?
The original version of WannaCry attempted to connect to iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com and then terminated if successful. Other variants then emerged with hex edited domains, or with that section hex-edited out entirely. But why was it there? It could just be a bit of unfinished code. It might be intended as an anti-detection measure, but it’s been pointed out that it doesn’t just do a DNS lookup it expects to create a TCP connection to the domain too. If there’s no TCP connection then WannaCry will execute the payload anyway. It could just be the hacker’s way of “having fun” with their malware – let people think it’s stopped and then push out the variants. Who knows?
How much has been paid out in ransom?
Not very much. So far over 200,000 people have been infected, and only 292 (or less?) have paid the ransom. That’s 0.1%. The three wallets are: 12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw, 13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94, and 115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn. About $109,000 or USD 81,000 has been paid in total so far. At 292 people though that averages at significantly less than USD 300 per ransom – going by the actual dollar figure only 270 people or less have paid up at the time of writing.
Is it a State actor?
Possibly. You will have heard that North Korea has been identified as a possible culprit. The problem though is that any competent hacker can make their code look like it came from North Korea, China, Russia, the USA, whomever they want.
So what’s their motivation?
You might think that the crypto-ransomware developers are simply highly motivated to be paid hefty ransoms. Well, most professionals don’t believe that to be a huge motivation. Just look at the program for a start: it encrypts types of documents that are important and valuable to their owners. They could steal sensitive documents actually if they had wanted to, but they didn’t. So you heard about the NHS in the UK having patient information encrypted – that’s a huge problem for them – but can you imagine how much worse it would have been if the malware developers had stolen millions of confidential medical files, and then ran a real extortion racket like was run against Ashley Madison?
Then, they provide you with all the information you’ll need to get your files back, assuming you pay up. They give detailed instructions on how to use Bitcoin, they helpfully put the decryption program everywhere on your system so you can always find it, and they give you a wall-paper in case your antivirus removes the decryption program. And the program is translated into 28 languages as well to ensure that you can read it:
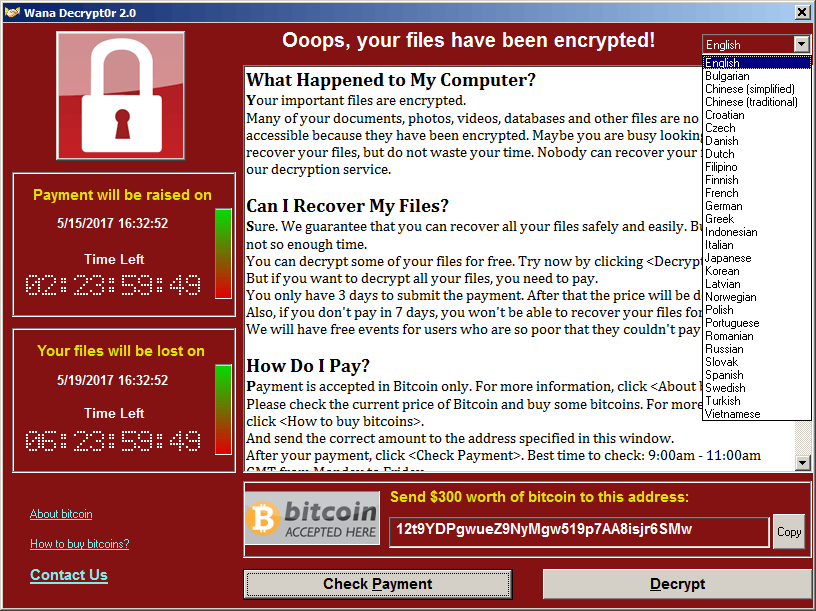
Their set-up is not particularly well designed to receive payments, which is why they’ve received so little. Plus they have to manually verify payments on their end because they didn’t put in an automated system (ie unique bitcoin identifiers) to make it easy for them to verify. And it’s not exactly going to be easy for them to get their bitcoins. But here’s the thing, malware has been around for a very long time before the concept of ransomware. So they are unlikely to care much about actually getting paid, in fact they tell you explicitly if you’re so poor you can’t afford the ransom there will be a chance to get your in six months.
Whatever their motivations are, it’s not money. At least not primarily. It’s been pointed out that leaked NSA cyberweapons have been used to turn computers into large botnets to mine bitcoins, and that was far more lucrative strategy for cybercriminals than this method. But what we can say is that they have put a lot of effort into their program – they want to get their name out, I don’t think they care whether people pay the ransom or not, they will probably give out the master key after a few months.
Did people click malicious links in emails?
This is the most misreported aspect of WannaCry. It is able to spread itself directly though the internet to any vulnerable computer that it finds. We don’t know how the NHS in the UK got infected, but it is possible that the worm spread across the internet by connecting to just one vulnerable PC or internet server across port 445, and then once it got on the network it can infect all the vulnerable PCs it finds on the ethernet. And that’s actually a larger problem for organisations than it is for home users, because it will be trying to connect through your IP address which is assigned to your router, but organisations often assign public IPs to computers. And they have to for servers. So yeah, we don’t know, but we do know that the this crypto-malware spreads directly across the internet without people needing to click any links if their system is vulnerable. That’s how bad this exploit is! Again though, if you’re behind a home router you’re probably safe.
Is it really the worst ransomware attack yet?
Yes. I chose my words carefully, it’s not necessarily the worst cyber attack, but it is the worst ransomware attack. What has made it so bad is that people on vulnerable networks do not have to click any links, as the malware spreads laterally as a worm. If you have this on your computer it will eventually try connecting directly to every single public IP in the internet – starting at 0.0.0.0 and ending at 255.255.255.255. Obviously that’s a simplified explanation, it randomises its IP selection, but yes every computer with the worm – all 200-300,000 of them – will eventually try to connect to every single IP on the internet. And it wouldn’t take that long either, as there’s only 4 billion IPs to try.
So it’s not an understatement at all to put the blame squarely on the US Government/NSA. And this is just the beginning – the ShadowBrokers (the hackers that hacked the NSA and released their cyber weapons) said they have yet more cyber weapons to release.
[…] through a malicious email campaign, with no evidence whatsoever to backup their claims. I rightly called it for what it was, and pointed out that the malware had the ability to spread itself directly to any vulnerable […]